Detecting New Network Devices with Python and Tkinter
UPDATE: I made a better version of this tool with server implementation here.
Today I felt like building a python 2.7 script that would enumerate a network along with alert me to the presence of a new device.
I limited my project to functions in the standard library.
So something lightweight and okay fast is a ping sweep. From an early post I included the Linux command for a sweep. I used this command along with the python commands to execute the ping sweep along with storing the results in a variable.
new = commands.getoutput('for i in {'+MIN+'..'+MAX+'}; do ping -c 1 -t 1 '+PREFIX+'.$i | grep "from"; done')
Following, I used some regular expressions to pull out the IP addresses detected in a given prefix range.
tmp = re.findall(PREFIX+"\.(\d+)", str(new)) #Pull out IP addresses from the ping results
Put that in a loop with some comparison data and you have a script that prints an alert whenever a new device is detected.
import commands, re |
There are a few short comings in the code but that’s the basic idea.
Now take this further, I hooked it up to a GUI with enumeration information! The new beastly application constantly flips through NMAP scan results of devices found connected to the network and displays the results in a GUI. I even placed a picture in the GUI. I call this app, the Hindenburg, its kind of hacked together.
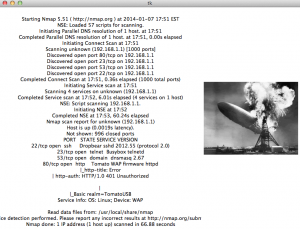
t = self.label1.cget(“text”) t = self.label2.cget(“image”) found = scanNetwork() photo = PhotoImage(file=”picture.gif”) for f in found[:-1]: #Loop through all but the last item self.label1.config(text=f) self.label1.update() self.label2.config(image=photo) self.label2.update() time.sleep(15) self.label1.config(text=found[-1]) #the last item doesn’t require the sleep, it takes enough time to run the scans self.label1.update() self.label2.config(image=photo) self.label2.update() self.after(1, flipping()) def scanNetwork(): app = flipGUI() |
It’s ideal for an environment where it can just sit on the screen without much of any type of activity going on. If you are enumerating the entire network, there will be a lag… it happens.