Intel RAID 5 on Windows 8.1
I upgraded by Windows 8 to Windows 8.1 a couple of months ago and since the change I was getting blue screens (of death…) consistently.

This issue was do to a piece of memory that was incorrectly over written, my RAID drivers were also failing. There really wasn’t anything important on my Windows partition so I decided to delete the partition and reinstall Windows 8.1 as a fix. There are helpful debugger tools to deal with this along with memory tests but it was just as easy for me to delete and start over.
The following instructions apply to an Intel Motherboard.
Enabling RAID (I already had my RAID setup, so I didn’t need to perform these steps since it is configured on the hardware level.)
- Turn on the computer and during the first screen that flashes the manufacturer name (the screen before the Windows logo) enter the BIOS menu. The screen flashes quickly and for those who don’t know how to enter this screen, it’s normally a F key. The manufacturer screen normally has on it a list of key options, just look for the one that will get you to the BIOS configuration (Don’t worry if you miss it, just keep shutting down the machine and turning it back on until you get it). For me, the Intel key was “F2”.
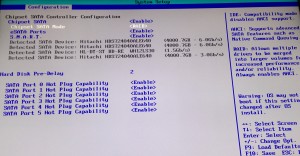
- Under the configuration tab in the BIOS, set the “Chipset SATA Mode” to RAID. Directions on how to change values are displayed on the right hand side of the screen.
- Save changes and exit the BIOS screen (ESC key).
Configuring RAID Volumes (Once again I already had this setup.)
- Reboot the computer. There should now be an additional screen that appears between manufacturer screens when you start the machine up. This lists all your RAID volumes.
- Quickly, press CTRL-I to get to the RAID configuration utility while the screen is up. This was actually tricky for me, I had to make multiple attempts. For some reason, I could not get this to work on my bluetooth keyboard but it worked with another keyboard… some bug. Even with a different keyboard, I basically held down CTRL and went crazy pressing “i” over and over and over again.
- In this window you can create RAIDS! Choose option 1 to create your volumes or look at the other available options for different functions.
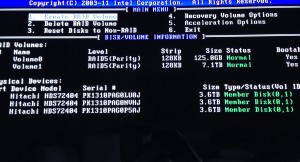
- My settings consist of two bootable RAID 5 volumes across my three ~4TB (3.6TB actual) hard drives. One with 125GB and the other with 7.1TB. The screenshot below shows my setup for your reference. Depending on your setup (RAID 5 requires at least 3 hard drives), you may want to do some research into RAID and your options. I chose 5 because it is supported by my motherboard and provides mirroring/striping. So it optimizes parallel communications and provides redundancy. In the case that one of my hard drives fails, I won’t loose anything. If two hard drives fail… I’m screwed. Basically, you have some protection from failure but still replace bad hard drives ASAP.
Install Windows
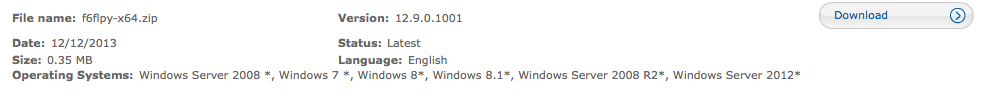
- Download the Intel RAID drivers from their website and put them on a USB device. The screenshot above shows the driver I downloaded. Keep the USB plugged in during the following steps.
- I had a DVD with a Windows 8.1 ISO burned to it. This was placed into the computer before I shut it down. I then turned the computer on and again during the manufacturer/first screen, I hit the “F10” key to select from where to boot. Most of the time, by default you boot from the Windows partition on your hard drive. However, this time, I wanted to boot from my install DVD containing Windows 8.1.
- It took awhile to load the Windows menu, but once it did, I chose to “Install.”
- The next few screens deal with entering your license key and junk.
- Once I was prompted for Default or Advanced setup. I chose Advanced. This was because I needed to mess with the partitions.
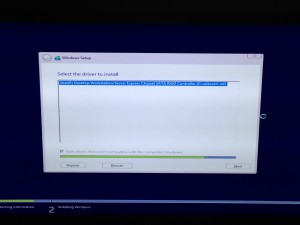
- The next screen will show the existing partitions but we have RAID going on and to make the install aware of this, we need to provide the drivers. In the current window, look for and select “Load driver.”
- I pointed the device to my USB to search for drivers. Once it found my Intel RAID driver, I selected it and clicked “Next.”
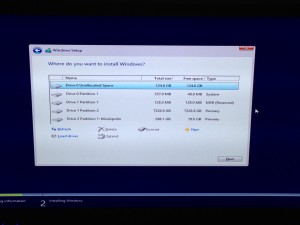
- After a few minutes, you will be returned to the partition window and you should see you RAIDs correctly.
- Format a new partition for your Windows (I deleted the previous). In my setup, I have 8 TB of hard drive space. I dedicated 124 GB to my Windows partition and the remainder to a partition I call “cabinet.” This is where I store my documents, media, etc. Windows does have a problem with creating a partition greater than 2TB. These drives must use GPT. This page discusses more on GPT. If this is what you plan to do, don’t partition the larger now, wait to use the Windows disk utility described in the link.
- Continue and let Windows install. Was completed, install drivers as needed. Intel has a tool that helps with this process.
There you have it!