Tomato Shibby Guest Wireless
I want a guest network to mess around with, I mean what are guests for after all?
What other reasons are there for having a guest network?
Well, say you don’t want to give out the password to your actual home network. You may want to limit activity of guests. You do not want guests to be able to communicate with personal devices on your network. You might have some malicious/untrustworthy friends and you want to keep yourself safe. So many reasons.
Worry not peoples, there is an easy way to set this up on Tomato Shibby and most other new router firmwares! The following steps use the tomato firmware web UI. By default, the UI can be accessed on 192.168.1.1 by a computer connected wirelessly to the router.
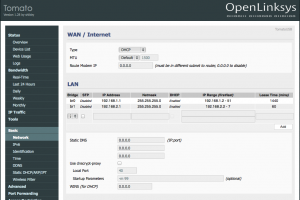
First thing is first, a new bridge has to be greater for this guest network. This bridge can be created in the Basic -> Network section under LAN. Simple click ‘Add’ and enter in your desired settings.
The bridge I created (br1), is pictured above. It is set to use IP addresses 192.168.2.2-192.168.2.7 with the router hosting on 192.168.2.1. I’m only allowing up to 6 guests. I don’t want my experience to get bogged down by guests so I limit the amount of addresses available to them hence limiting the number of guests able to connect. Also, I set the lease time for guests to 60 minutes, they don’t need a long lease time. Save your progress.
Sweet, so I now have this bridge. Now I must assign it to a VLAN.
“In computer networking, a single layer-2 network may be partitioned to create multiple distinct broadcast domains, which are mutually isolated so that packets can only pass between them via one or more routers; such a domain is referred to as a virtual local area network, virtual LAN or VLAN” (Wikipedia).
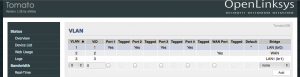
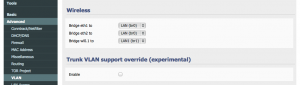
I don’t want guests accessing my stuff, so I will put them on a separate VLAN. Create a VLAN (for me it was 3) and assign the new bridge (br1) to it in Advanced -> VLAN under VLAN.
In my setup above, I’m not expecting guests to connect directly to a port on the router so I did not configure any of them. I expect guests to just connect wirelessly. Save your progress after setting this up.
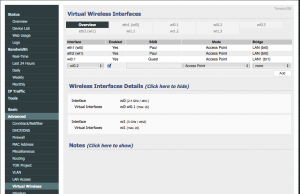
Now time to set up the wireless SSID for the guests. Go to Advanced -> Virtual Wireless. Add the wl0.1 interface (or whatever one you want to use) and set it to use the new bridge (br1). Give it any SSID you want, I chose to call mine Guest, as seen below. Save it.
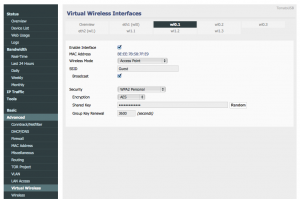
You can configure settings for the wireless interface by selecting the coordinating tab (wl0.1) from the top of the page. For instance, you might want to give it security. For now, I gave mine security but I don’t think I’ll keep it. Save it.
Finally, double check all is set correctly in Advanced -> VLAN.
Basically, look to make sure the right bridge is setup to the right wireless interface. Save it.
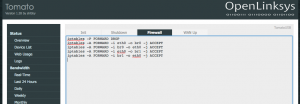
Next to make sure my guest VLAN users cannot access my private network devices I added a few block forwarding IP table rules. To do this, add the following commands in Administration->Scripts under Firewall:
iptables -P FORWARD DROP iptables -A FORWARD -i eth0 -o br0 -j ACCEPT iptables -A FORWARD -i br0 -o eth0 -j ACCEPT iptables -A FORWARD -i eth0 -o br1 -j ACCEPT iptables -A FORWARD -i br1 -o eth0 -j ACCEPT
These rules first drop all forwarding communications. Following, the next rules set the firewall to allow communications between both bridges and the external world (eth0) only. This way the networks cannot talk to each other but still have internet connectivity. Save and you’re done with the basics!
I went ahead and added a few extra things like a splash page for guests and I also limited their bandwidth activity. I’ll explain how to do this in a later post, this one is too long.